
VPN operation and maintenance solution
Background introduction
With the rapid expansion of business, many large enterprises, institutions, governments, and organizations have emerged with numerous branch structures throughout the country, and some branches or subsidiaries are even established overseas. There is a large amount of data transmission between branches and headquarters, and internal resources such as OA systems, financial systems, quotation systems, and data platforms are frequently accessed, and the data flow is also very large. Therefore, how to provide a comprehensive security solution from the sending end, the transmission link to the receiving end is the focus of major enterprise information managers.
1. The cost of dedicated line is high, and the risk of publishing site is high
When considering the interconnection between headquarters and branches, information managers of many enterprises first think of leasing dedicated lines to realize the interconnection between headquarters and branches. However, the monthly rental costs of tens of thousands to hundreds of thousands of dollars make network administrators Tired to apply for the fee to the company's leaders. If all the IP addresses of internal servers are mapped to the Internet, and branch employees can access these services freely through the Internet, then it is tantamount to presenting all the company's network communication process under the eyes of people with ulterior motives, and there is no secret at all.
2. Simple VPN device function is simple
After abandoning the wealthy and handsome plan of leased private lines, smart CIOs turned to select special virtual private line network equipment to build secure tunnels for secure interconnection. For example, IPSec VPN equipment can build secure IPSec tunnels between headquarters and branches. However, with the company's many expansions, many of my colleagues in the front are not at the customer's place most of the time, or on the way to visit the customer, and there is no fixed office area to access company resources through IPSec VPN. If you want to solve this problem, you also need to deploy SSL VPN equipment that supports secure terminal access. Deploying pure IPSec VPN or SSL VPN separately in the network not only has security drawbacks in the device itself, but also as the number of devices increases, the cost will rise sharply, and device management will become more and more complicated.
3. Intranet security is as important as VPN connection
Deployed equipment supporting multiple VPN tunnel technologies to meet the security access requirements of fixed office areas of branch offices and mobile users, but it also brought hidden network security risks with continuous network attacks and rapid virus spread. The management of branches is relatively loose. It is common to use U disks and mobile hard disks to copy data. Portable computers are free to access the Internet at any access point, and there is no habit of regular anti-virus and Trojan-checking. If an employee connects a device infected by a virus or a Trojan horse to the company network, it will not only affect the network of the branch, but also the network of the whole company. Because the VPN interconnection between the company networks makes the branch and the headquarters Access is as convenient as a local area network, and the spread of viruses and Trojan horses is also very convenient.
On the other hand, since most branches have fewer personnel, each branch has limited IT investment. If you purchase basic security equipment such as firewalls, IPS, AV protection, etc., it is also a huge expense. How to choose a cost-effective The solution has become a problem that information security managers have to face. Therefore, for security products, integrated comprehensive solutions are the development trend.
4. As the number of VPN devices increases, maintenance becomes more and more complicated
There are more and more branches. Although it brings business growth to the enterprise, it also brings challenges to network management. The level of network administrators in each branch is different, and the headquarters cannot monitor the operation of branch VPN equipment. If there is a problem with the VPN equipment of the branch, you can only send someone from the headquarters to support it, which not only increases the labor cost, but also cannot solve the problem in the first time. Because branch offices have a certain degree of difficulty in maintaining VPN equipment, how to better manage and maintain remote VPN equipment has become an important issue that needs to be considered in VPN solutions.
5. Diversified network environment and complex network deployment
Due to the diversification of services provided by network operators, the way for headquarters and each branch to access the network is different. Some branches access the network through fixed IP assigned by the operator, while some branches may use ADSL. The IP access network is dynamically allocated in the method; some branches can be directly connected to the headquarters, and there are NAT address translation equipment between some branches and the headquarters, which may hide the VPN device address. Therefore, the complex network environment puts forward higher requirements for the convenience of VPN devices to access the network.
6. The poor experience of VPN network access affects efficiency
After careful analysis and careful selection, the VPN network has been successfully deployed. All branch offices and mobile office workers can safely access company resources through VPN, but VPN technology is an encrypted tunnel established on the public network infrastructure, so In the long-distance transmission network environment such as transnational, trans-provincial, and trans-operator, the efficiency of VPN access is very low due to high packet loss and large network delay. Frequent visits to the intranet OA system are stuck, refilling of financial statements after failing submission, and data downloading is abnormally slow, etc., which affects the work efficiency of branch offices and mobile office workers, and network managers become the target of company employees' complaints.
solution
—Economic and safe VPN network interconnection solution
Each enterprise has different requirements for network interconnection according to different business scales. For branch users with fixed office areas, they prefer IPSec VPN networking; for branches without fixed office areas, companies with all mobile employees are more inclined to choose SSL VPN networking; for existing fixed office areas, there are also a large number of For companies with mobile office workers, they need to choose both IPSec VPN and SSL VPN networking solutions; for some small and medium-sized enterprises or branch offices that have greater cost pressures, they can only choose to provide both security protection and IPSec VPN and SSL VPN. A low-cost integrated solution for secure interconnection.
On the basis of careful investigation of the above-mentioned customer needs, the NGFW product launched by Fortinet can provide economical and secure VPN network interconnection solutions with one device, including multiple secure tunnel technologies such as IPSec VPN, SSL VPN and L2TP over IPSec VPN. It can also provide a full range of security protection programs, including various network attack blocking, intrusion detection and protection systems, virus scanning, URL filtering and other security protection functions. Fortinet's NGFW products are in line with the general trend of network security equipment integration and integrated development.
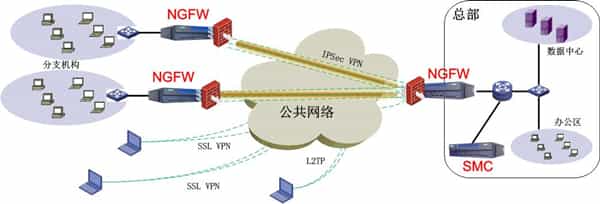

Headquarters deployment plan:
The Fortinet NGFW product is deployed at the network exit of the headquarters, which mainly provides external IPSec VPN tunnel interfaces to realize the connection with branch IPSec VPN tunnels; provides SSL VPN access portal interfaces to realize the security of mobile office users' access to the intranet Access; provide comprehensive security protection functions, including traditional firewall functions, IPS, AV, URL filtering and other security protection functions, to achieve the security isolation between the internal network and the external network; at the same time, the VPN acceleration function is turned on to ensure the performance experience of external access.
The Fortinet Security Management Center device SMC is deployed inside the NGFW of the headquarters. This device mainly implements comprehensive management functions such as configuration management, security status monitoring, and intelligent analysis of NGFW products across the entire network. Information security managers in the headquarters can use this device to implement unified deployment, monitoring and analysis of all border NGFW products.
Branch deployment plan:
A Fortinet NGFW product is deployed at the network exit of the branch, which mainly realizes the docking with the headquarters IPSec VPN tunnel. The intranet users of the branch access the resources in the headquarters network like a local area network. At the same time, it provides comprehensive security protection functions, including traditional firewall functions, IPS, AV, URL filtering and other security protection functions, to realize the security isolation between the internal network of the branch and the external network.
Fortinet VPN solution value
1. VPN and security technology integration
With the continuous expansion of the scale of enterprises, more and more attention is paid to information security. It is not only necessary to ensure the confidentiality of data transmitted between each branch and the headquarters, but also to ensure that network attacks such as viruses and Trojan horses cannot spread freely within the network between the branches and the headquarters. Therefore, enterprises must not only have multiple methods of VPN interconnection, but also have comprehensive security protection functions.
Fortinet NGFW products can provide different VPN tunnel technologies such as IPSec VPN, SSL VPN and L2TP over IPSec VPN, which can not only satisfy the interconnection between branches and headquarters, but also satisfy the safe access of mobile office workers. Multiple VPN technologies are implemented on one device, which is convenient for users' network deployment and device maintenance. At the same time, Fortinet’s NGFW product is the first real next-generation firewall product in China. While providing basic protection functions of traditional firewalls, it can also maintain high performance to realize the security protection functions of IPS, AV, URL filtering and other next-generation firewalls. .
2. Centralized equipment management improves network maintenance efficiency
The network equipment deployments of some large enterprises, institutions, governments, and organizations are distributed. Headquarters deploy high-end VPN equipment, and branch offices must also deploy relatively low-end VPN equipment. It is not necessary to manage so many professional VPN equipment. Little challenge. With the development of technology, the functions provided by VPN devices become more and more powerful, so if you want to make all these functions work, the configuration becomes more and more complicated. However, the security management personnel of the branch are responsible for the maintenance of all network equipment and other office equipment in the branch, and the management level of the security equipment is uneven. A problem with the VPN equipment of the branch caused the network to be blocked, and the local security manager was unable to locate and troubleshoot the problem. The slow speed and low efficiency of network problem resolution greatly affect the company's normal business development.
The security management center SMC equipment provided by Fortinet can realize functions such as centralized management of equipment, monitoring of the entire network status, and global threat analysis, which can help users who have deployed multiple NGFW products to better reduce management costs and control the security status of the entire network. , And realize powerful threat warning and analysis capabilities on the basis of network-wide big data mining.
3. VPN traffic is accelerated to improve user access experience
With the massive deployment of VPN devices, users have achieved secure access to company resources, but the experience of accessing resources has become a concern for users. Because when external employees access the internal network, if the access speed is slow and the experience is poor, the first complaint is the network management department. The root cause of the poor VPN network access experience is that the VPN tunnel is a virtual private network built on the public network infrastructure. Therefore, the bandwidth bottleneck of the headquarters outlet, the scattered multiple branches, and the local area network applications across the WAN will affect the VPN users. Access to the network has an impact.
Fortinet NGFW optimizes the TCP connection process through unilateral acceleration technology. Through the congestion avoidance mechanism, the unilateral acceleration protocol can quickly and accurately estimate the available bandwidth in the network, and determine the congestion avoidance window based on the estimated value, so as to maximize the use of network bandwidth. The unilateral acceleration protocol can quickly detect the packet loss, and can quickly and accurately retransmit the packet, which can effectively improve the bandwidth utilization in the case of large delays and poor network conditions. The sender can use it in the rapid recovery process by changing To increase the sending rate, provide greater throughput.
4. Flexible networking and easy deployment
The network environment of each customer is very different. Each branch has a different way of accessing the network through the operator. The VPN device of the branch may be hidden behind the NAT address translation device. Some scenarios require the VPN device to act as a gateway on the network. In some scenarios, VPN devices are not allowed to be connected to the network. The brand of IPSec VPN devices in the headquarters is different from that of branches. Therefore, VPN equipment needs to support networking and deployment in various network environments.
Carefully analyze various application scenarios of users, and adapt to customer needs through a variety of convenient and flexible VPN networking methods developed on NGFW products. Mainly reflected in the following functional characteristics:
The support center is a fixed IP, and the branch is a dynamic IP networking mode such as ADSL.
Support DDNS networking mode where both ends of IPSec tunnel are dynamic IP
Adopt the international standard IPSec protocol to ensure the compatibility of the interconnection of equipment from different manufacturers.
Support multiple deployment methods such as bypass and routing.
Support the intercommunication between branches, set up access control, and provide intra-network isolation and authorization management.
Support the certificate method as an authentication method for branch interconnection to strengthen access security.

