
Sandbox solution
The financial industry is developing rapidly. While providing diversified financial services to the society, it must also be timely and scientifically guarded against the risks it brings. Vulnerabilities are the core of the entire security game. Soxiang Technology’s systematic products can help customers eliminate high-risk vulnerabilities, business security risks, etc. before the application goes online, so that the application goes online without disease and eliminates the security problems from the source.
The security sandbox, as an independent logical storage space, separates the storage domain of the enterprise application box on the device from the individual, restricts the data communication between the two parties, and strengthens the security of the enterprise application data. "Enterprise sandbox" is a logical concept that can help end users understand a series of security functions and master their use. However, at the technical level, due to the differences between OSs and the implementation methods on each platform are different , The operation is also slightly different.
The security sandbox can provide an extra layer of password protection and data encryption. In addition to the power-on password of the device, when any APP in the security sandbox is used; the password verification of the second-level password is required. At the same time, all data entering the sandbox is encrypted and stored. Even when the device is lost and jailbroken, it can read the files in the sandbox, but the files have been encrypted and the contents of the files cannot be cracked. This is especially important for BYOD scenarios where jailbreaking threats are greater.
Suoxiang Technology is the first in the industry to launch a complete set of self-developed "service + tools + platform" security development full-process solutions.
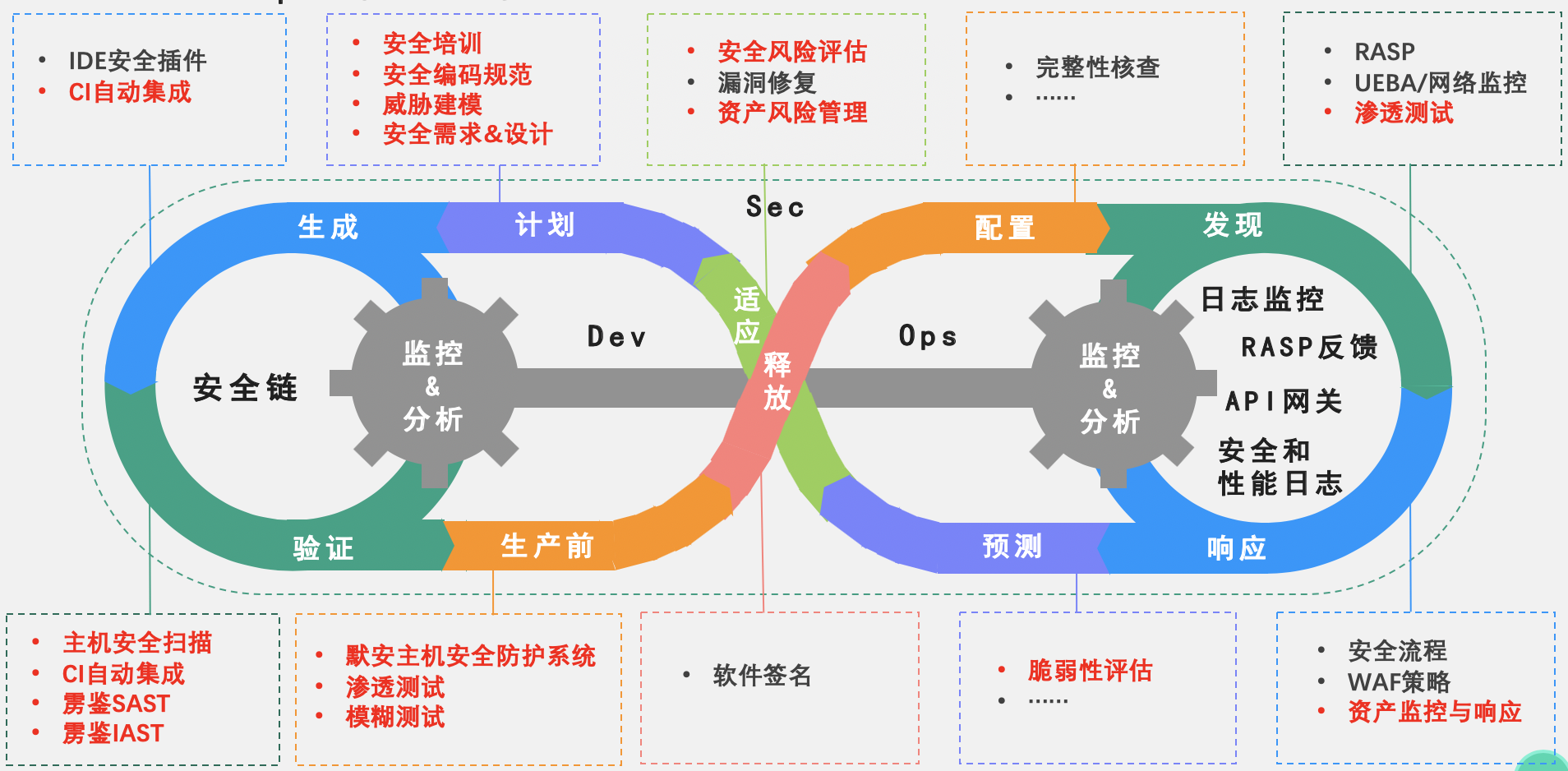
The solution can be seamlessly integrated with the DevOps process, and integrated with the code warehouse, Jenkins platform, Bug management platform (Jira, etc.), and test environment. Both the SAST module and the IAST module can be integrated with the CI/CD platform; the SAST module vulnerability detection engine automatically pulls and scans the code by integrating with the code warehouse to cover the security issues in the coding phase; the IAST module collects information initiated by the CI/CD platform Automated functional testing of traffic, analysis and vulnerability detection of traffic, covering security issues in the testing phase; security risks are output to the CI/CD platform or bug management platform through API, and are closely integrated with the platform.
Among them, the real vulnerabilities unearthed by the IAST module are 50% more than traditional vulnerability scanning tools; the solution also supports software component analysis (SCA), which can find security problems of third-party components; and has the ability to detect business logic vulnerabilities with low false positives. The solution has gained a good reputation on the client side in the fields of finance, Internet, smart manufacturing, and electric energy.
Case (1) A city commercial bank
Case background
At present, it has more than 10 branches, more than 300 business outlets, and 8,000 employees across the country, and its services cover the Yangtze River Delta region. Open banking is one of the bank’s main businesses. It is acquired based on Internet scenarios and uses open API technology to cooperate with various online platforms to realize payment, financial products or other open services, which increases business risk exposure and lengthens the entire risk In the chain of management, the security responsibilities faced by banks before the business goes online are increasing day by day.
Needs and pain points
◆ Internet business makes security face higher challenges;
◆ Faced with the dilemma of API technology, data is difficult to crawl;
◆ Over-reliance on manual investigation;
◆ Strict delivery quality management and high safety management cost.
Program content
◆ Mo'an "service + tools" development safety process plan
Solution value
◆ The code data flow detection mode breaks through the "API dilemma"
The function test traffic is collected through the code data flow mode to trigger vulnerability detection, which can cover one-time interfaces such as encryption and verification codes, and solves the "API dilemma" of traditional crawlers.
◆ Automated security testing to meet the scope of vulnerability detection in the industry
Solve the problem of incomplete coverage of common vulnerability tests, find common vulnerabilities in the system as soon as possible, and avoid many security risks.
◆ Accurately discover vulnerabilities and achieve zero false positives of security risks
Through IAST, a security test link is established in development and testing, effectively forming a security closed loop, quickly discovering vulnerabilities, locating security risks, and measuring security vulnerabilities with zero false positives, reducing the difficulty of security testing.
◆ Visual management, empowering the safety of software development
Through the visual unified management interface, it helps the security department and the testing department to establish a bridge, clearly displays the project's security testing and the discovery of vulnerabilities, and tracks the repair of the vulnerabilities.
Case (2) A listed company
Case background
The company is a listed company focusing on the R&D, production and sales of healthy food appliances. With technological changes, more and more intelligent small home appliances have become home appliances unicorns in the Internet of Things era, and have become an important part of people's lives. As a domestic mainstream brand, the company's business volume is increasing day by day, and the hidden safety hazards in the development process need to be resolved urgently.
Needs and pain points
◆ In the Internet of Things era, the business of small home appliances is increasing day by day, and security risks are high;
◆ Safety test procedures and specifications need to be optimized urgently;
◆ Solve the problem of business going online with illness.
Program content
◆ Mo'an "service + tools" development safety process plan
Solution value
◆ Establish a security test link in the development test through IAST, replacing the manual penetration link, helping companies quickly find loopholes and detect security issues during the development process, and achieve zero false positives for loopholes;
◆ Established a set of safety regulations for the R&D process, effectively forming a safety closed loop in the work process, and meeting the needs of the R&D team for business safety self-examination;
◆ In the safety test link, Moan's technical support team responded immediately after a problem occurred, which was unanimously recognized by the customer.
Case (3) Large Group
Case background
The group was established in 1984. After more than 30 years of development, it has become one of the largest residential development companies in China. Its business covers the Pearl River Delta, the Yangtze River Delta, the Bohai Rim and the three major urban economic circles as well as the central and western regions, with a total of more than 50 major cities. In mid-city cities, the scale of sales continues to rank first in the industry in the world.
Needs and pain points
◆ Avoid security risks before the group's intelligent manufacturing business is fully launched;
◆ Solve the problem that the safety of the research and development process is difficult to promote;
◆ Detect security issues and ensure delivery quality.
Program content
◆ Mo'an "service + tool + platform" develops a safe full-process solution
Solution value
◆ A unified online inspection process, implanting security advantages for the application system before going online;
◆ Low false positives and high detection of vulnerabilities, greatly reducing verification costs and risks;
◆ Zero threshold, non-intrusive security detection, breaking the organizational boundary between R&D and security;
◆ The overall R&D safety capability has reached a new level.
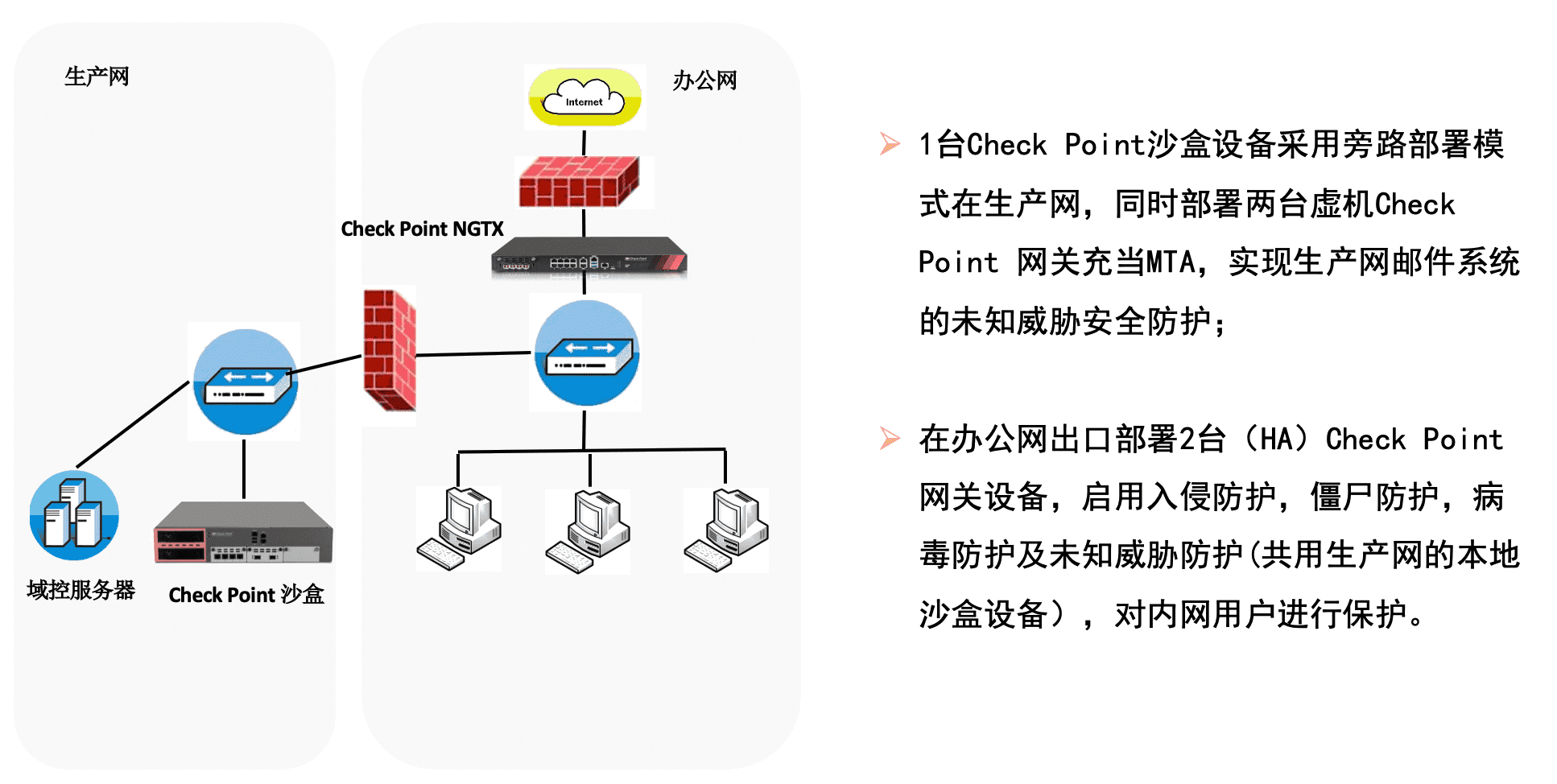
Solution deployment case:
上一篇:無

