Address: 1st Floor,Building 4, 1088th, Huyi highway, Shanghai TEL:021-31080981 Email:soline@soline.com.cn P.C.:201802
Citrix receiver cloud desktop solution
In the traditional IT mode of PC office, problems such as easy damage to PC hardware, multiple system failures, and cumbersome software updates will bring management workload and IT operation and maintenance costs. Using the cloud desktop diskless office system, a one-stop desktop cloud solution can effectively improve deployment efficiency, simplify desktop operation and maintenance workloads, and at the same time ensure information security and achieve smooth mobile office.

1. Desktop virtualization solution goals: current office PC usage status, network viruses, no authority management, high PC maintenance costs, slow system and other issues. Therefore, the cloud desktop diskless office system must be used to solve the problem.

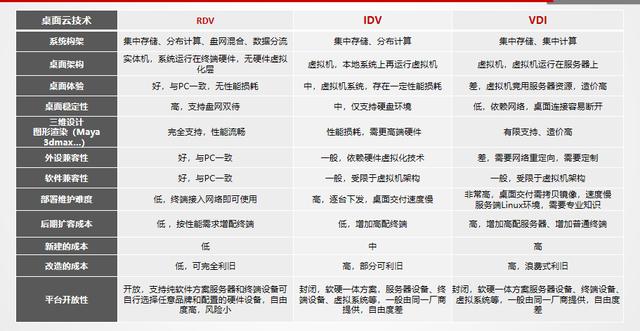
2. Desktop virtualization function architecture: with control layer, access layer, and computing layer. Smoother, more stable, more efficient and safer.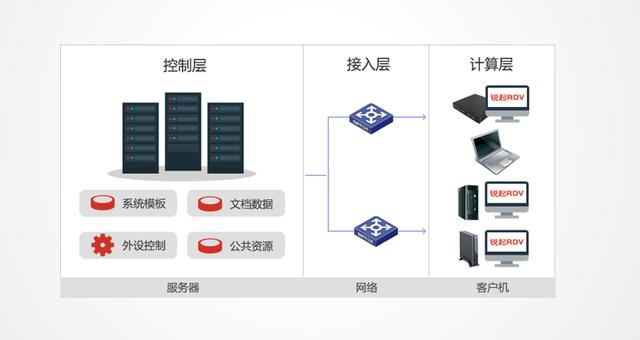
3. System principle-centralized storage/distributed computing: extensive and simplified terminal equipment support, you can use various equipment, computers, clients, etc. to log in.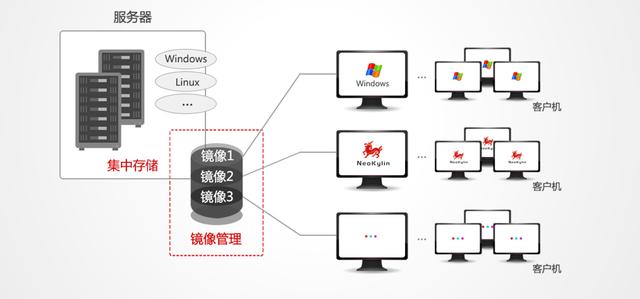
4. System principle-disk network integration: unified configuration, the use of security administrators can uniformly configure and manage all desktops and applications in the back-end data center, avoiding traditional management difficulties and high costs caused by terminal distribution.
5. Product interface, the distribution is more concise and clear.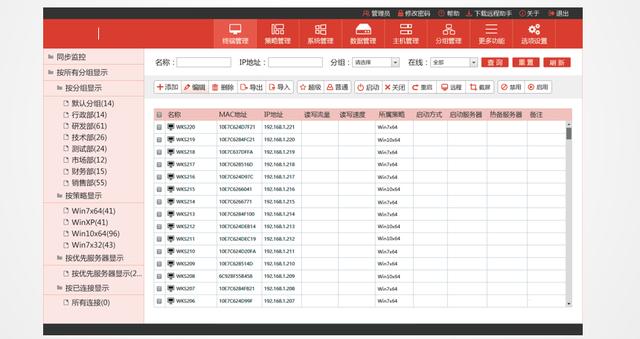
6. Product functions: more complete functions.
7. Desktop management: Since the operating system is all deployed on the server, it only takes about 20 seconds for the user to log in to their desktop from the terminal boot. Compared with the traditional PC, the login time of 1-2 minutes is greatly shortened, and it will not appear. The more software is installed, the slower the startup time.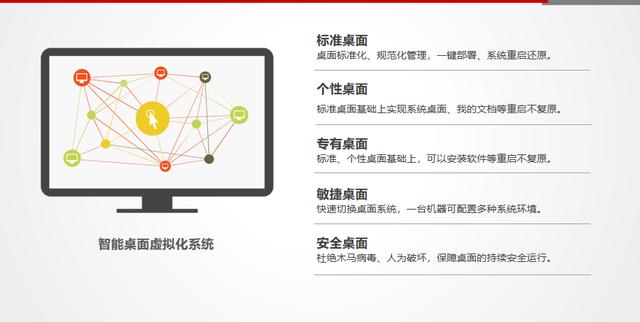
8. Data management: All data and calculations occur in the back-end data center. Confidential data and information do not need to be transmitted through the network, which increases security and ensures that user data will not be lost.
9. Peripheral control supports voice recognition devices, functional keyboards, USB devices, multi-monitor plug and play, which expands the use of virtual desktops on peripherals, meets the needs of different users for the use of external devices, and also satisfies centralized management and control. Prevent data leakage and viruses.
10. Security management and control: It has multiple management and control methods, which is more secure. Enhance the possibility that user data will not be lost.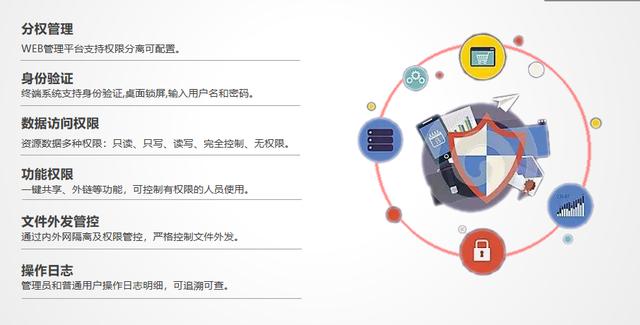
11. Operation and maintenance management: It is an access office, with simpler operation, more efficient desktop management, and more flexible user access.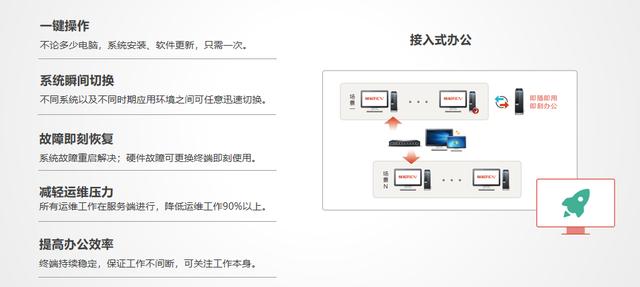
12. More functions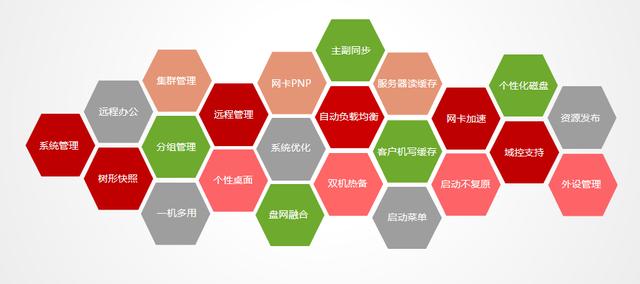
13. Smooth experience: Since all operating systems are deployed on the server and are local data, the operation will be very smooth.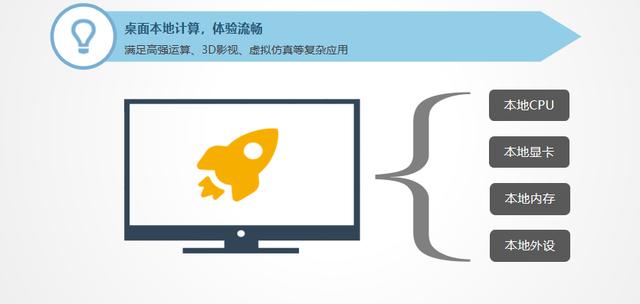
14. Tree-shaped snapshot: The system uses tree-shaped snapshots for management and realizes one-click switching of applications. It is a more professional, high-quality, and efficient technology.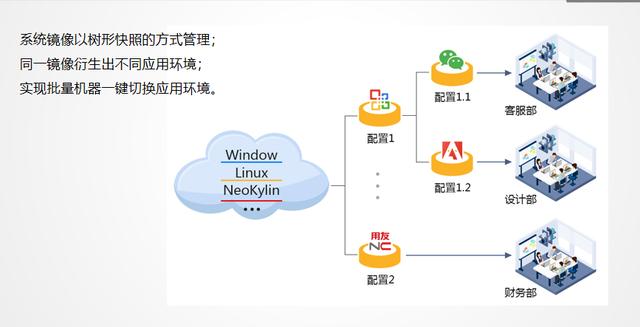
15. Fine-grained file permissions: unified configuration, you can remotely access the desktop system, and get the same experience as the PC; and the administrator can easily complete all management tasks only in the data center.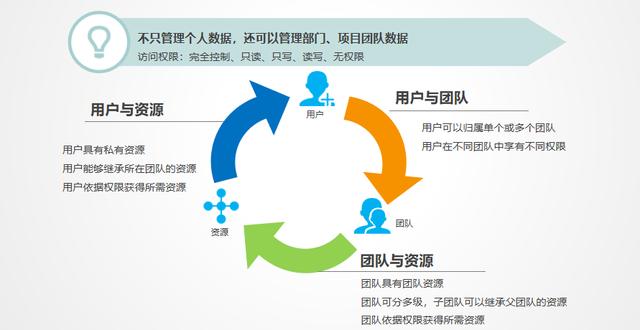
16. All-round protection of data security: There are functions such as multi-level recycle bins and data encryption, which increase security and ensure that user data will not be lost.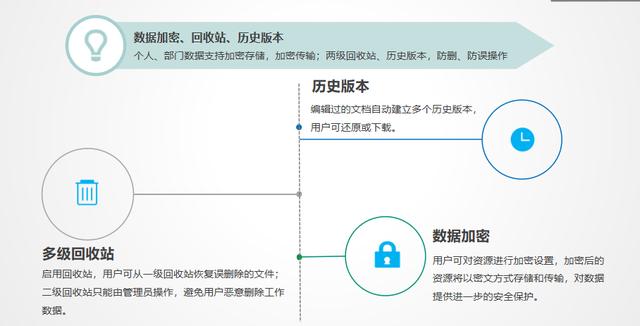
17. Compatible with all: centralized storage/distributed computing, extensive and simplified terminal equipment support, compatible with all peripherals.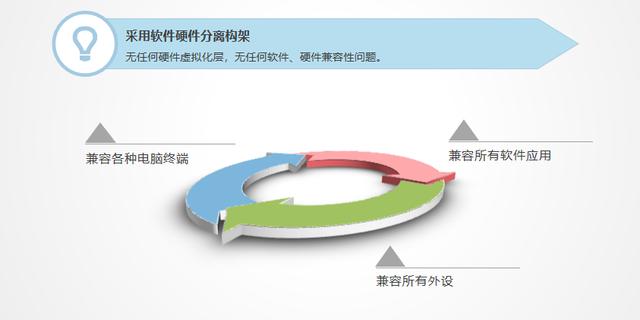
18. Seamless management: transparent application, more peace of mind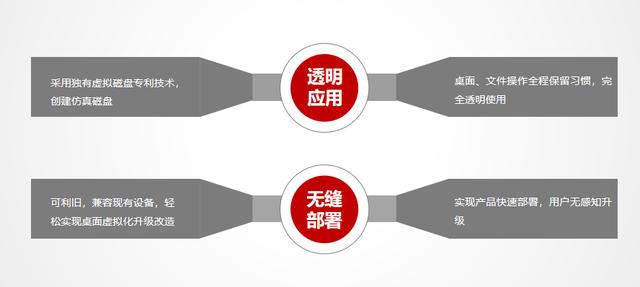
19. Large-scale high availability: Compared with traditional methods, virtual desktops use a large number of lightweight terminals and centralized background computing resources, which can reduce the overall system operating cost by about 80%, and with linear expansion, the benefits and advantages will increase. Outstanding, so it can be used on a large scale.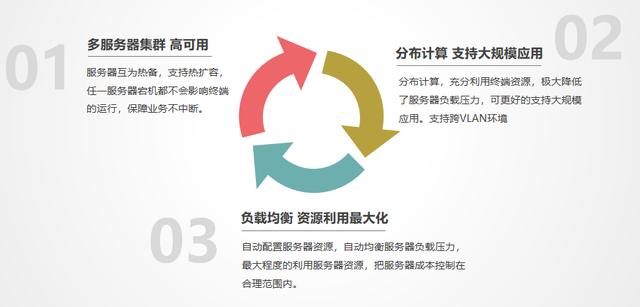
20. Product value: It can meet the requirements of desktop operation and maintenance personnel to use any device to access software anytime and anywhere, and bring more effective unified management and configuration of application software for enterprises. At the same time, the important data of the enterprise are safe and core data can be prevented from leaking.
21. Comparative advantage